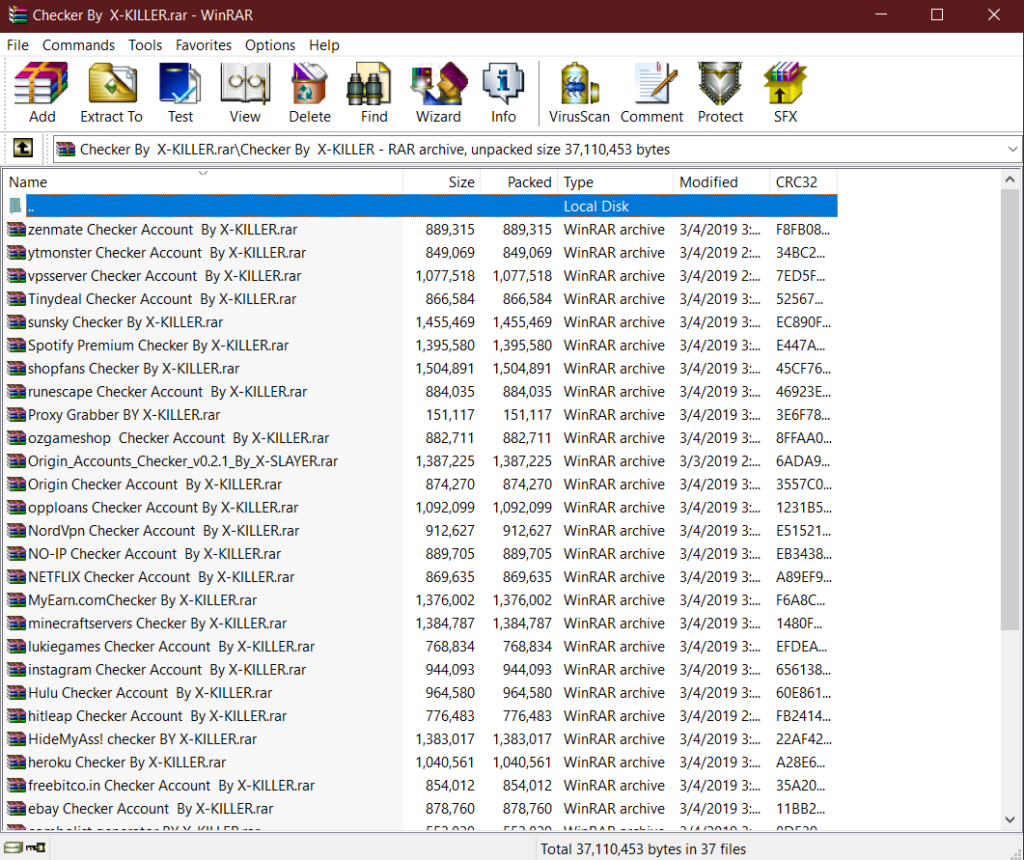
Files
37 files
-
CRYPTER PRIV8
By
 dEEpEst
This crypt is elbowed in Visual Basic 6, it has no dependencies.
dEEpEst
This crypt is elbowed in Visual Basic 6, it has no dependencies.
Use DES encryption.
Other options are:
EOF Data Realing PE Cahnge EOP
The ratio of AV's can not be offered because right now there is no service provider that offers us multi scanners that do not distribute samples to AV's, "the remedy would be worse than the disease".
However we ensure a good ratio, 3/31. Note that this crypter has been created since 0, and is not used by anyone or used by anyone other than you.
Have a happy encrypted.
Scan Update:
4 purchases 17 downloads
(0 reviews)Updated
-
(0 reviews)
Submitted
-
43GB Hacking Tools
By
 dEEpEst
Download: FREE Download users PRIV8
dEEpEst
Download: FREE Download users PRIV8
Note* link available until he dies. Run tools on VM
18 downloads
(0 reviews)Submitted
-
[7.42 GB] Leaked Database & Combos & Dorks & More (2022)
By
 dEEpEst
MEGA .NZ LEAK DATABASE COMBOS DUMPS MORE
dEEpEst
MEGA .NZ LEAK DATABASE COMBOS DUMPS MORE
Link: Download Free for users PRIV8
27 downloads
(0 reviews)Updated
-
Paid Ethical Hacking Course Noob To Pro
By
 dEEpEst
Paid Ethical Hacking Course Noob To Pro
dEEpEst
Paid Ethical Hacking Course Noob To Pro
*This Course Including Maximum Videos To Learn Ethical Hacking From Scratch. It Will Help you To Understand Everything About Ethical Hacking.
*Download LINK : Download Free for users PRIV8
17 downloads
(0 reviews)Submitted
-
Hackpack | Premium Stuff'S | Massive Collection
By
 dEEpEst
HACKPACK | PREMIUM STUFF'S | MASSIVE COLLECTION
dEEpEst
HACKPACK | PREMIUM STUFF'S | MASSIVE COLLECTION
This Hack Pack Includes 13 GB Of Hacking Tutorials ,Tools ,BlackHat Guides , Accounts ,Bombers ,BotNet Etc..
LINK - Download Free for users PRIV8
tools must be run in a secure environment, they are also not backed up
35 downloads
(0 reviews)Submitted
-
BlackHatProTools Hidden Content Leak
By
 dEEpEst
BlackHatProTools Hidden Tools And Content Leak
dEEpEst
BlackHatProTools Hidden Tools And Content Leak
HQ Leak Fo BlackHatProTools
Link: Free download for Users PRIV8
123 downloads
- blackhatprotools
- hidden
- (and 2 more)
(0 reviews)Updated
-
Advanced Web Hacking Tools
By
 dEEpEst
Tools Contains:
dEEpEst
Tools Contains:
Havij
NetDatabaseScanner
Open Web Spider
Quick Web
Site Hog
Snippets Manager
Spider mail
SQL Injection
SQL Map Project
The Mole
ZeroTeam ™ MD5 Password Encryptor
Acunetix Web Vulnerability Scanner
Advanced Deface Creator 1.3
Anonymous DNS Extractor-2013
Anonymous FTP Stealer
Anonymous Text Encrypter
Anonymous Tinypaste Uploader
Ashiyane SQL Scanner
Base64 Image Encoder-Decoder
BTI Admin Page Finder v2
BTI HTML Encoder-Decoder
BTI Multi Site Checker
BTI Reverse IP Domain Check v2
ChromePasswordDecryptor
CSS Minifier v2
Deface Page Created
Dork Searcher Setup v1091
dorkinj
DorkTools
Eternals WebBrowser
Explode Web Scanner
ezDataBase_Defacer
Fiddler Web Debugger Setup
Gklspy
Google URL Extractor
Gr3eNoX LFi Exploiter
Hacker’s Browser v2.0
Injection Framework - Automatized Sql Injection Tool
Iron Web application Advanced Security testing Platform
Joomla Security Scanner
JSQL-Injection
Mass Dork Scanner v1.0.0.1
Multi Vuln Checker
nmap
Spider mail
SQL Exploiter Pro v2.10
SQL Helper
SQLI-Hunter_v1.1
SQLI-Hunter_v1.2
SQL-Inject-Me-master
sqlmap_win_v01
sqlmap-0.9
sqlninja-0.2.6-r1
SQLSentinel_v_0.3
Surf Excuse
Survey Bypasser
Tiny URL Shortener
Vulcan Cleaner
Vuln Hunter
vulnerability master
wapiti-2.3.0-win32-standalone
Warbot VersaoSQL Tool v1.0 Alpha Build 6
Web Source Tools
WebCruiser
WebCruiserPro
Websecurity Scanner 0.9
Website Blocker v2
WebSurgery-Setup-1.1.1
XCodeExploitScannerSept
xSQL SCanner
Size: 141MB
Download: Free for Users PRIV8
62 downloads
(0 reviews)Submitted
-
BLACKHAT HACKING < TOOLS & TUTORIALS [ 10Gb ]
By
 dEEpEst
BLACKHAT HACKING < TOOLS & TUTORIALS
dEEpEst
BLACKHAT HACKING < TOOLS & TUTORIALS
MEGA Package Of Creditcard, Paypal, Amazon, Ebay, Fraud Package
LINK :- Download Free for Users PRIV8
103 downloads
(0 reviews)Updated
-
100+ DDOS Tools
By
 dEEpEst
DDOS Tools Pack
dEEpEst
DDOS Tools Pack
List Of Tools:
360BooterOff
A Flooder
Anonymous High Orbit Ion Cannon v1.1
Black’s Booter
ByteDOS v3.2, v3.2.1
D@RK Doser 1.0
DarkMajic Flooder
DDOS v2.0.0 Rev B x64
DDOS v2 Mike12
DDVniek’s Hacker ToolBox 1.2
Death n Destruction
Destroy DOS
Donut HTTP Flooder
DOS Attacker Alpha 1.1
DOS HTTP 2.5.1 – Doser #3
Dragon
DrBlowFish’s_DOS
ExploitAttack
HC Doser
Hight Orbot Cannon v1.1
Hoic
Hoic #6
HTTPDOSTool
iDisconnect
Infamous Stresser
IP Grabber
IP Grabber And DDOSer
Jay’s Booter
Jay’s Booter v6.0
Lion Attacker – DDOSer #4
xDDOSer
And Many More..
Download Free for Users PRIV8
69 downloads
(0 reviews)Submitted
-
(0 reviews)
Submitted
-
Big Database Combolist Private/Public HQ 700 GB
By
 dEEpEst
Big Database Combolist Private/Public HQ 700 GB
dEEpEst
Big Database Combolist Private/Public HQ 700 GB
Link Download: Free for users PRIV8
323 downloads
(0 reviews)Submitted
-
HAXOR Cracking Pack 2020
By
 dEEpEst
HAXOR Cracking Pack 2020
dEEpEst
HAXOR Cracking Pack 2020
Haxor Cracking Pack
Haxor Pack Contains Cracking Tools And Checkers Pack By darkdante, m1st, MR.v1per, redeye, rubiconT, shaOnkristof ,Xkiller ,xPolish ,X-Risky, X-Slayer and KIDuX
And Many More
________________________________________
Download free for users PRIV8
80 downloads
(0 reviews)Submitted
-
Máster Hack Pack
By
 dEEpEst
1. Netflix cracking (full tutorials+tools)
dEEpEst
1. Netflix cracking (full tutorials+tools)
2.Amazon prime video method
3.Deezer method
4.Eros now subscription method
5. Instagram panel trick
6.Steam cracking tool
7.VIU+VOOT trick with download
8.PUBG UC pass trick
9.Carding PDFs for noobs
10.AMEX accessing PDF
11.CC cashout
12.ATM hack
13.Instagram account hack
14. WhatsApp admin hack
15.Netflix Cracker
16. Free 1 Month Netflix Trick ( You Can Create Unlimited Account )
17.Free Netflix using PayPal ( Video Tutorial )
18.Free Amazon Prime Trick + Video Tutorial
19.Hotstar Cracking Trick (Video Tutorial)
20.How To Bypass Link Shortner
21.Instagram Liker
22.Snow’s YouTube Bot
23.YouTube View Booster Bot
24.YouTube Blazzer
25. 50 Android Hacks
26.Amazon Gift Cards
27.Paypal Method
28.Ebay Method
29.Free Amazon Gift Card Method
30.Free Pizza Method
31.Flipkart Carding Tutorial
32.How To Get Fresh Valid Proxy List For Cracking
33.How To Get A Free Master Card
34.How To Get Referrals
35.Bypass Gmail Mobile Verification Trick
36.Bypass Android Pattern Lock Using ADB
37.Get Refund Of GiftCard
38.Facebook Hacking Ebook
39.Get Things From Ebay For Free
40.SEO Secrets
41.Guide To Make Money Online
42. Hack Hotmail
43.Hack Gmail
44.Hacking Methods
45.CC Generator
46.CC Checker
47.Crack WEP in Linux
48.Get Massive YouTube Traffic
49.Get Passes To Pornsites
50.Hack WEP WiFi Password
51.Kick Someone Of A Wireless Network
52.Make $1000’s A Week With Torrents
53.Make A Phisher For A Website (Facebook/Instragram/Etc)
54.Make Easy Money As An eBay Affiliate
55.Make Multiple Gmail Accounts With Only 1 Account
56.How To Make Mozilla 30 Times Faster
57.USA Whatsapp Number Trick
58.Collection Of Rare Hacking Ebooks
59.Starbucks Method
60.How To Call Someone From His Own Number (Caller Id Spoofing)
61.Transfer PP Balance Method
62.YouTube RED Trick
63.Gaana Mod App
64.Netflix Mod App (Look a Like)
65. Saavn Mod App
66. Express VPN Mod App
67.7 Reasons a Credit Card Is Blocked
68. Amazon Carding Method + Video Tutorial
69.What is Carding?? (Video)
70.Basic Carding TutoBal
71.Phishing Tutorial
72.Easy Cardable Sites List
73.Find Local BIN’s
74. Carding For Noobs
75.Carding Online Tools And Website
76.PayPal Carding
77.Wallmart Carding
78.Amazon Carding (Video Tutorial)
79. eBay Carding (Video Tutorial)
80.Full process of carding
Free download for users PRIV8
36 downloads
(0 reviews)Submitted
-
stealer dEEpEst Stealer Bitcoins
By
 dEEpEst
-------------- INTALL --------------
dEEpEst
-------------- INTALL --------------
Open "svchost.exe" with a hexadecimal editor,
locate the default BTC address and replace it with yours.
Then run "svchost.exe" on the PC you want it to work.
With each start of windows the thief will start,
to clean the PC and everything is as at the beginning,
you must run "Killer DSB.exe" and restart the PC.
After this there will be no trace.
___#___By dEEpEst___#___
0 purchases 0 downloads
(0 reviews)Updated
-
CRACKING PACK 2020 (2GB)
By
 dEEpEst
CRACKING ARCHIVE -CRACKING TOOLS,CONFIGS,PROXYS,COMBOS .netflix cracking .cracking tutorials free bundle pack mega
dEEpEst
CRACKING ARCHIVE -CRACKING TOOLS,CONFIGS,PROXYS,COMBOS .netflix cracking .cracking tutorials free bundle pack mega
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
59 downloads
(0 reviews)Submitted
-
Leaked All Tools of Crackti.info
By
 dEEpEst
Leaked All Tools of Crackti.info
dEEpEst
Leaked All Tools of Crackti.info
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
141 downloads
(0 reviews)Submitted
-
Uʟᴛɪᴍᴀᴛᴇ HᴀᴄᴋPᴀᴄᴋ Fʀᴏᴍ DʀᴇᴀᴍMᴀʀᴋᴇᴛ Oɴ DᴀʀᴋWᴇʙ
By
 dEEpEst
Uʟᴛɪᴍᴀᴛᴇ HᴀᴄᴋPᴀᴄᴋ Fʀᴏᴍ DʀᴇᴀᴍMᴀʀᴋᴇᴛ Oɴ DᴀʀᴋWᴇʙ
dEEpEst
Uʟᴛɪᴍᴀᴛᴇ HᴀᴄᴋPᴀᴄᴋ Fʀᴏᴍ DʀᴇᴀᴍMᴀʀᴋᴇᴛ Oɴ DᴀʀᴋWᴇʙ
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
94 downloads
(0 reviews)Submitted
-
MEGA HACKPACK [ 691MB ]
By
 dEEpEst
MEGA HACKPACK [ 691MB ]
dEEpEst
MEGA HACKPACK [ 691MB ]
- Crackers
- Cypters and Binders
- Dork Scanners
- Dos+DDoser++Flooders
- Forensic Tools
- KeyLoggers
- Misc. Web Tools
- Network Tools
- RATs
- SMS & Email Bombers
- VPNs & Security
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
35 downloads
(0 reviews)Updated
-
[Biggest Cracking Pack] Over 50+ Tools | Checkers | Crackers | Combos
By
 dEEpEst
[BIGGEST CRACKING PACK] OVER 50+ TOOLS | CHECKERS | CRACKERS | COMBOS
dEEpEst
[BIGGEST CRACKING PACK] OVER 50+ TOOLS | CHECKERS | CRACKERS | COMBOS
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
23 downloads
(0 reviews)Submitted
-
All X-Killer Checker Pack 2019 (Best Cracking Pack) +35 Checkers
By
 dEEpEst
ALL X-KILLER CHECKER PACK 2019 (BEST CRACKING PACK) +35 CHECKERS
dEEpEst
ALL X-KILLER CHECKER PACK 2019 (BEST CRACKING PACK) +35 CHECKERS
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
22 downloads
(0 reviews)Submitted
-
Mega Cracking Pack 500Mb+ Of Cracking Tools
By
 dEEpEst
MEGA CRACKING PACK 500MB+ OF CRACKING TOOLS
dEEpEst
MEGA CRACKING PACK 500MB+ OF CRACKING TOOLS
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
9 downloads
(0 reviews)Submitted
-
BEST CRACKING PACK | Over 50 Cracking Tools/Checkers
By
 dEEpEst
CHECKERS
dEEpEst
CHECKERS
Depfile Checker by m1st
Nordvpn Checker by m1st
Spotify Checker by m1st
Teacherspayteachers Checker by m1st
Zengaming Checker by RubiconT
WWE Checker by RubiconT
Uplay Soft Checker By RubiconT
UFC Checker by RubiconT
HMA Checker by xPolish
Udemy Checker by RubiconT
Toluna Checker by RubiconT
Tidal Checker by RubiconT
Spotify Checker by RubiconT
Soundcloud Checker by RubiconT
Skillshare Checker by RubiconT
Coinify Accounts Checker By X-SLAYER
GearBest AccountsChecker By X-SLAYER
Scribd Checker by RubiconT
Betfair Accounts Checker By X-SLAYER
Paysafecard Checker By RubiconT
Pandikey Checker by RubiconT
NFL Checker by RubiconT
Newage-bank Checker By RubiconT
Netflix Checker by RubiconT
NBA Checker by RubiconT
Napster Checker by RubiconT
Lynda Checker by RubiconT
Hulu Checker by RubiconT
HBO Now Checker by RubiconT
Grammarly Checker By RubiconT
Gokano Checker by RubiconT
Directv Now Checker by RubiconT
Deezer Checker by RubiconT
Crunchyroll Checker by RubiconT
Chegg Checker by RubiconT
CBS Checker by RubiconT
Bonusbitcoin Checker by RubiconT
Blizzard Checker by RubiconT
Bigstockphoto Checker by RubiconT
WWE Brute Checker_ShaOnKrisTof
UPlay Brute Checker_ShaOnKrisTof
Toluna Brute Checker_ShaOnKrisTof
Successbux_ShaOnKrisTof
Steam Brute Checker_ShaOnKrisTof
Spotify Brute Checker_ShaOnKristof
Origin Brute Checker_ShaOnKrisTof
Netflix Brute Checker_ShaOnKrisTof
Hungama Brute Checker_ShaOnKrisTof
Hotstar Brute Checker_ShaOnKrisTof
Hotspot Shield VPN Brute Checker_ShaOnKrisTof
Ganna Brute Checker_ShaOnKrisTof
Deezer Brute Checker_ShaOnKrisTof
Crunchyroll Brute Checker_ShaOnKrisTof
Cut-URL Brute Checker_ShaOnKrisTof
BTC Clicks Brute Checker_ShaOnKrisTof
Adfocus Brute Checker_ShaOnKrisTof
Adfly Brute Checker_ShaOnKrisTof
Wish.com Checker By X-SLAYER
Wordpress Checker By X-SLAYER
Steam Accounts Checker By X-SLAYER
Spotify Accounts Checker By X-SLAYER
SendPulse Accounts Checker By X-SLAYER
Recharge.com Checker By X-SLAYER
qqtube Accounts Checker By X-SLAYER
Origin Accounts Checker By X-SLAYER
Pinterest Accounts Checker By X-SLAYER
MyCanal Accounts Checker By X-SLAYER
HMA AccountsChecker By X-SLAYER
Gokano Accounts Checker By X-SLAYER
Origin API Cracker Coded By MR.ViPER - v3.1
Steam API Cracker Coded by MR.ViPER - v3.0
Uplay API Cracker Coded By MR.ViPER - v3.0
PayPal Software by Dark Dantes
Instagram Reg Checker Update
Golden-tea.me by Dark Dantes
Discogs Brute by Dark Dantes
Chase Bruteforce
Cdkeyhouse
Amazon Reg Checker by Dark Dantes
Redeye's Spotify Checker v2.2
Redeye's Netflix Checker 1.1
Redeye's Minecraft Checker
Redeye's Hulu Checker
Redeye's Email Checker
Redeye's Digital Ocean Checker
Redeye's Deezer Checker
Redeye's CoinPot Checker
Bet365 Accounts Checker By X-SLAYER
Redeye JustCloud Checker
CoinPot Checker by xPolish
Discord Checker by xPolish
HMA Checker by xPolish
Hulu Checker by xPolish
Amazon Valid Email Checker By X-SLAYER
Minecraft BruteChecker by xPolish
PlayStation Registration by xPolish
Spotify Checker by xPolish
VyprVPN Checker by xPolish
WWE Checker by xPolish
Fortnite Accounts Checker BY X-SLAYER
Zenmate Checker by xPolish
Facebook Accounts Checker By X-SLAYER
Alexa Accounts Checker By X-SLAYER
TOOLS
Steam Account Info By X-SLAYER
TXT Files MERGE by X-SLAYER
Total Proxy Leecher v0.1 By X-SLAYER
SQLi SLAYER v404
Proxy Grabber v0.2 By X-SLAYER
Proxy Leecher v0.2 By X-SLAYER
Proxy Checker v0.2 By X-SLAYER
FreeProxy_ShaOnKrisTof
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
34 downloads
- tools/checkers
- over
- (and 3 more)
(0 reviews)Updated
-
Business & Marketing Stuff | Tools | Scripts | Programs [VIP DOWNLOAD COLLECTION] - [19.31 GB]
By
 dEEpEst
Business&Marketing Stuff | Tools | Scripts | Programs
dEEpEst
Business&Marketing Stuff | Tools | Scripts | Programs
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
30 downloads
(0 reviews)Submitted
-
CEH v10 Tools
By
 dEEpEst
Herramientas de laboratorio para v10 CEH:
dEEpEst
Herramientas de laboratorio para v10 CEH:
CEHv10 - Laboratorio de Requisitos
CEHv10 Módulo - Huella y Reconocimiento
CEHv10 Módulo - Escaneo Redes
CEHv10 Módulo - Enumeración
CEHv10 Módulo - Análisis de vulnerabilidad
CEHv10 Módulo - Sistema de Hacking
CEHv10 Módulo - Amenazas de malware
CEHv10 Módulo - Oler
CEHv10 Módulo - Ingeniería Social
CEHv10 Módulo - denegación de servicio servicio
CEHv10 Módulo - secuestro de sesiones
CEHv10 Módulo - IDS Evadir, cortafuegos, y honeypots
Módulo CEHv10 - Cortar los servidores web
Módulo CEHv10 - Aplicaciones web de hacking
CEHv10 Módulo - inyección SQL
Módulo CEHv10 - Cortar Redes inalámbricas
CEHv10 Módulo de hacking - Plataformas móviles
Módulo CEHv10 - Cloud Computing
CEHv10 Módulo - criptografía
━━━━━━━━━━━━━━━━━━━━━
You can download these books and guides for free if you are a PRIV8 user.
15 downloads
(0 reviews)Submitted
.webp.8407a83ac96563f75e1c428a1f0d4c3e.webp)
.webp.9a04cec050a656fab081ac190f971c3f.webp)