Search the Community
Showing results for tags 'enumeration'.
-
Gato, or GitHub Attack Toolkit, is an enumeration and attack tool that allows both blue teamers and offensive security practitioners to evaluate the blast radius of a compromised personal access token within a GitHub organization. The tool also allows searching for and thoroughly enumerating public repositories that utilize self-hosted runners. GitHub recommends that self-hosted runners only be utilized for private repositories, however, there are thousands of organizations that utilize self-hosted runners. Who is it for? Security engineers who want to understand the level of access a compromised classic PAT could provide an attacker Blue teams that want to build detections for self-hosted runner attacks Red Teamers Bug bounty hunters who want to try and prove RCE on organizations that are utilizing self-hosted runners Features GitHub Classic PAT Privilege Enumeration GitHub Code Search API-based enumeration GitHub Action Run Log Parsing to identify Self-Hosted Runners Bulk Repo Sparse Clone Features GitHub Action Workflow Parsing Automated Command Execution Fork PR Creation Automated Command Execution Workflow Creation SOCKS5 Proxy Support HTTPS Proxy Support [hide][Hidden Content]]
-
LinkedIn enumeration tool to extract valid employee names from an organization through search engine scraping. Names can be formatted in a defined naming convention for further security testing. CrossLinked simplifies the processes of searching LinkedIn to collect valid employee names when performing password spraying or another security testing against an organization. Using similar search engine scraping capabilities found in tools like subscraper and pymeta, CrossLinked will find valid employee names and help format the data according to the organization’s account naming convention. Results will be written to a ‘names.txt’ file in the current directory for further testing. Changelog v0.1 Added tools directory with name gen scripts and O365 user validation. Bug fixes / improvements. [hide][Hidden Content]]
-
- crosslinked
- v0.1
-
(and 3 more)
Tagged with:
-
VPN Overall Reconnaissance, Testing, Enumeration and Exploitation Toolkit Overview A very simple Python framework, inspired by SprayingToolkit, that tries to automate most of the process required to detect, enumerate and attack common O365 and VPN endpoints (like Cisco, Citrix, Fortinet, Pulse, etc...). Why I developed it Make the VPN spraying phase much quicker and easier. Also, due to its flexibility, this tool can be added to an existing OSINT workflow pretty easily. What the tool can do for you Vortex mainly provide assistance with performing the following tasks: User Search and Collection LinkedIn Google PwnDB Password Leaks PwnDB Main Domain Identification OWA S4B/Lynk ADFS Subdomain Search Enumeration Bruteforce VPN Endpoint Detection Password Spraying/Guessing attacks O365 Lynk/S4B ADFS IMAP VPNs Cisco Citrix FortiNet Pulse Secure SonicWall Search profiles on Social Networks Instagram Facebook Twitter TikTok Onlyfans [hide][Hidden Content]]
-
Anubis, a subdomain enumerator, and information gathering tool. It collates data from a variety of sources to provide one of the most comprehensive tools for subdomain enumeration. It pulls subdomains from public sources, indexed search results, and AnubisDB, a centralized, open API for subdomains. It is able to identify all key servers behind the domains and output any IPs of interest. For instance, running the same command as above with the -p flag gives us all the unique resolved IP addresses, which allows a security researcher to get a more comprehensive idea of the scope of their target. It is also able to extract information from less used, but potentially rewarding avenues, including DNSSEC subdomain lists and Zone Transfers. Changelog v1.1.3 Fix DNSSEC and Nmap scans [hide][Hidden Content]]
-
A Subdomain Enumeration and Validation tool for Bug Bounty and Pentesters. Key Features OSINT + Subdomain Bruteforcing Capable of handling outputs from multiple tools Handling False Positives and Filters subdomains with same resolutions. Checking for Server Banners and Ports Incredibly Fast Handling domains with larger scopes Port Scanning [hide][Hidden Content]]
-
Description Enumeration is designed for ethical hackers who want to build their skills in reconnaissance of targets and in optimizing their penetration testing. In this course, instructor Malcolm Shore teaches the basic methods of enumerating networks and targeting systems with common enumeration tools. Malcolm explains what enumeration is and gives you opportunities in the course for hands-on experience. He covers enumeration for local and remote hosts. Malcolm discusses how to enumerate web apps, the internet, and cloud resources. He also goes over how to use tools like SuperScan, NetScanTools Pro, Nmap, JXplorer, and more. [Hidden Content] [hide][Hidden Content]]
-
CrossLinked LinkedIn enumeration tool to extract valid employee names from an organization through search engine scraping. Names can be formatted in a defined naming convention for further security testing. CrossLinked simplifies the processes of searching LinkedIn to collect valid employee names when performing password spraying or another security testing against an organization. Using similar search engine scraping capabilities found in tools like subscraper and pymeta, CrossLinked will find valid employee names and help format the data according to the organization’s account naming convention. Results will be written to a ‘names.txt’ file in the current directory for further testing. Changelog v0.0.5 Initial release Extract employee names from LinkedIn via search engine scraping [hide][Hidden Content]]
-
- 5
-

-
- crosslinked
- v0.0.5
-
(and 3 more)
Tagged with:
-
0xsp mongoose red version is provided to assist your needs during cyber security simulation, by using this version you will be able to audit a targeted windows operation system for system vulnerabilities, misconfigurations and privilege escalation attacks. with node js support for web application API, it becomes much easier for installation and customization in timely manner, the windows sensor agent will communicate with application API to transfer results, and receive commands as bidirectional technique. the agent is able to identify and detect windows exploits by using windows update api and exploit database definitions modules, the new release will detect also the following vulnerabilities. CVE-2019-0836 CVE-2019-0841 CVE-2019-1064 CVE-2019-1130 CVE-2019-1253 CVE-2019-1385 CVE-2019-1388 CVE-2019-1405 CVE-2019-1315 CVE-2020-0787 CVE-2020-0796 CVE-2020-0797 Features web application built with NodeJS supports sqlite DB Lateral movements techniques. Bidirectional communication channel. video Plugins online packaging. Enhanced exploit detecter scripting engine. the weaponization of run-as-user windows api function. local network scanning and shares enumeration. lsass memory dumping technique (plugin). [hide][Hidden Content]]
-
- 1
-

-
- 0xsp-mongoose
- v2.2.1
-
(and 4 more)
Tagged with:
-
Domained – Multi Tool Subdomain Enumeration Domained is a multi tool subdomain enumeration tool that uses several subdomain enumeration tools and wordlists to create a unique list of subdomains that are passed to EyeWitness for reporting. This produces categorized screenshots, server response headers and signature based default credential checking. It is written in Python heavily leveraging Recon-ng. Download: [Hidden Content]
-
Turbolist3r - Subdomain Enumeration Tool With Analysis Features For Discovered Domains Turbolist3r is a fork of the sublist3r subdomain discovery tool. In addition to the original OSINT capabilties of sublist3r, turbolist3r automates some analysis of the results, with a focus on subdomain takeover. Turbolist3r queries public DNS servers for each discovered subdomain. If the subdomain exists (i.e. the resolver replied with an address), the answer is categorized as CNAME or A record. By examining A records, it is possible to discover potential penetration testing targets for a given domain. Likewise, the process of looking for subdomain takeovers is simple; view the discovered CNAME records and investigate any that point to applicable cloud services. Please do not use for illegal purposes. [HIDE][Hidden Content]]
-
- 1
-

-
- turbolist3r
- subdomain
-
(and 2 more)
Tagged with:
-
The TIDoS Framework The Offensive Web Application Penetration Testing Framework. Highlights :- Here is some light on what the framework is all about: - [x] A complete versatile framework to cover up everything from Reconnaissance to Vulnerability Analysis. - [x] Has 5 main phases, subdivided into __14 sub-phases__ consisting a total of __108 modules__. - [x] Reconnaissance Phase has 50 modules of its own (including active and passive recon, information disclosure modules). - [x] Scanning & Enumeration Phase has got 16 modules (including port scans, WAF analysis, etc) - [x] Vulnerability Analysis Phase has 37 modules (including most common vulnerabilites in action). - [x] Exploits Castle has only 1 exploit. `(purely developmental)` - [x] And finally, Auxillaries have got 4 modules. `more under development` - [x] All four phases each have a `Auto-Awesome` module which automates every module for you. - [x] You just need the domain, and leave everything is to this tool. - [x] TIDoS has full verbose out support, so you'll know whats going on. - [x] Fully user friendly interaction environment. `(no shits)` TIDoS is built to be a comprehensive, flexible and versatile framework where you just have to select and use modules. So to get started, you need to set your own `API KEYS` for various OSINT & Scanning and Enumeration purposes. To do so, open up `API_KEYS.py` under `files/` directory and set your own keys and access tokens for `SHODAN`, `CENSYS`, `FULL CONTACT`, `GOOGLE` and `WHATCMS`. Finally, as the framework opens up, enter the website name `eg. [Hidden Content]` and let TIDoS lead you. Thats it! Its as easy as that. To update this tool, use `tidos_updater.py` module under `tools/` folder. Flawless Features :- TIDoS Framework presently supports the following: Other Tools: net_info.py - Displays information about your network. Located under `tools/`. tidos_updater.py - Updates the framework to the latest release via signature matching. Located under `tools/`. TIDoS In Action: Lets see some screenshots of TIDoS in real world pentesting action: Version: v1.7 [latest release] [#stable] Upcoming: These are some modules which I have thought of adding: Some more of Enumeraton & Information Disclosure modules. Lots more of OSINT & Stuff (let that be a suspense). More of Auxillary Modules. Some Exploits are too being worked on. More info & Download: [hide][Hidden Content]]
-
- 1
-

-
- web-fuzzer
- reconnaissance
-
(and 4 more)
Tagged with:
-
Microsoft Windows suffers from an NTFS privileged file access enumeration vulnerability. Attackers possessing user-only rights can gather intelligence or profile other user account activities by brute forcing a correct file name due to inconsistent error messaging. View the full article
-
Linux enumeration tool for pentesting and CTFs with verbosity levels Unlike LinEnum, lse tries to gradualy expose the information depending on its importance from a privesc point of view. What is it? This script will show relevant information about the security of the local Linux system. It has 3 levels of verbosity so you can control how much information you see. In the default level you should see the highly important security flaws in the system. The level 1 (./lse.sh -l1) shows interesting information that should help you to privesc. The level 2 (./lse.sh -l2) will just dump all the information it gathers about the system. By default it will ask you some questions: mainly the current user password (if you know it 😉 so it can do some additional tests. How to use it? The idea is to get the information gradually. First you should execute it just like ./lse.sh. If you see some green yes!, you probably have already some good stuff to work with. If not, you should try the level 1 verbosity with ./lse.sh -l1 and you will see some more information that can be interesting. If that does not help, level 2 will just dump everything you can gather about the service using ./lse.sh -l2. In this case you might find useful to use ./lse.sh -l2 | less -r. You can also select what tests to execute by passing the -s parameter. With it you can select specific tests or sections to be executed. For example ./lse.sh -l2 -s usr010,net,pro will execute the test usr010 and all the tests in the sections net and pro. Use: ./lse.sh [options] OPTIONS -c Disable color -i Non interactive mode -h This help -l LEVEL Output verbosity level 0: Show highly important results. (default) 1: Show interesting results. 2: Show all gathered information. -s SELECTION Comma separated list of sections or tests to run. Available sections: usr: User related tests. sud: Sudo related tests. fst: File system related tests. sys: System related tests. sec: Security measures related tests. ret: Recurren tasks (cron, timers) related tests. net: Network related tests. srv: Services related tests. pro: Processes related tests. sof: Software related tests. ctn: Container (docker, lxc) related tests. Specific tests can be used with their IDs (i.e.: usr020,sud) Source & Download : [Hidden Content]
-
0xsp-Mongoose - Privilege Escalation Enumeration Toolkit (ELF 64/32), Fast, Intelligent Enumeration With Web API Integration Using 0xsp mongoose you will be able to scan a targeted operating system for any possible way for privilege escalation attacks, starting from collecting information stage until reporting information through 0xsp Web Application API. user will be able to scan different Linux os system at the same time with high performance, without spending time looking inside the terminal or text file for what is found, mongoose shorten this way by allowing you to send this information directly into web application friendly interface through easy API endpoint. project is divided into two sections server & agent . server has been coded with PHP(codeigniter) you need to install this application into your preferred environment, you can use it online or on your localhost. user is free to choice .also contribution to enhancing features are most welcomed. Agent has been coded as ELF with Lazarus Free Pascal will be released with (32, 64 bit) while executing Agent on targeted system with all required parameters. user is free to decide whether willing to communicate with Server App to store results and explore them easily . or he can also run this tool without Web API Connection. Agent Features High performance , stability , Output results Generated while executing no delays Ability to execute most of functions with intelligent techniques . results are being sent to Quick Web API Exception Handling . inbuilt Json Data set for publicly disclosed Exploits . Fast As Mongoose [Hidden Content]
-
- 1
-

-
- 0xsp-mongoose
- privilege
-
(and 3 more)
Tagged with:
-
ManageEngine ServiceDesk Plus version 9.3 suffers from a user enumeration vulnerability. View the full article
-
- manageengine
- servicedesk
-
(and 4 more)
Tagged with:
-
Zimbra Collaboration User Enumeration Script (CVE-2018-10949) How to use The argument --host must be the hostname or IP address of Zimbra Collaboration Web Application root page, and --userlist an list of usernames to check against it. root@kali# ./cve-2018-10949-user-enum.py --host [Hidden Content] --userlist /tmp/emails.txt And it should spill out valid e-mails! [Hidden Content]
-
- 2
-

-
- user
- collaboration
-
(and 6 more)
Tagged with:
-
CVE-2018-15473-Exploit Exploit written in Python for CVE-2018-15473 with threading and export formats Threading - default 5 If more than 10 are used, often the OpenSSH service gets overwhelmed and causes retries Single username evaluation via username parameter Multiple username evaluation via userList parameter Multiple username evaluation file output via outputFile parameter Multiple output formats (list, json, csv) via outputFormat parameter An example username input file is given in exampleInput.txt An example results output file in List format is given in exampleOutput.txt An example results output file in JSON format is given in exampleOutput.json An example results output file in CSV format is given in exampleOutput.csv Build the image: docker build -t cve-2018-15473 . Run the exploit: docker run cve-2018-15473 -h Delete containers and image: docker ps -a | awk '$2 == "cve-2018-15473" {print $1}' | xargs docker rm docker rmi cve-2018-15473 [Hidden Content]
.webp.8407a83ac96563f75e1c428a1f0d4c3e.webp)
.webp.9a04cec050a656fab081ac190f971c3f.webp)




 itsMe
itsMe
 dEEpEst
dEEpEst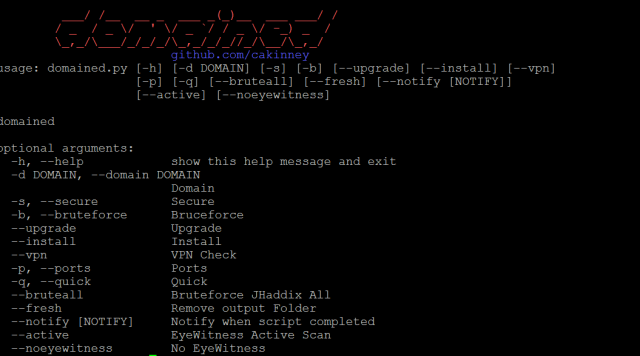


 1337day-Exploits
1337day-Exploits